Poison Ivy Remote Administration Tool Download - The requested documents will be made available to the general public, and this request is not being made for commercial purposes. Here in this post, i am mentioning about software program poison ivy which is actually a rat(remote administration tool), by which a hacker can access any server installed computer remotely.
Backdoorw32poisonivy Description F-secure Labs
How to use a rat program if you cannot port foward.
Poison ivy remote administration tool download. A remote administration tool (rat) that bypasses the security features of a program, computer or network to give unauthorized access or control to its user. Records mentioning or describing the remote administration tool (rat) known as poison ivy. The 'check' command can be used to determine if the c&c target is using the default 'admin' password.
This report spotlights poison ivy (pivy), a rat that remained popular and effective years after its release, despite its age and familiarity in it security circles. 2shared gives you an excellent opportunity to store your files here and share them with others. Poison ivy hacking tools software, free download pc.
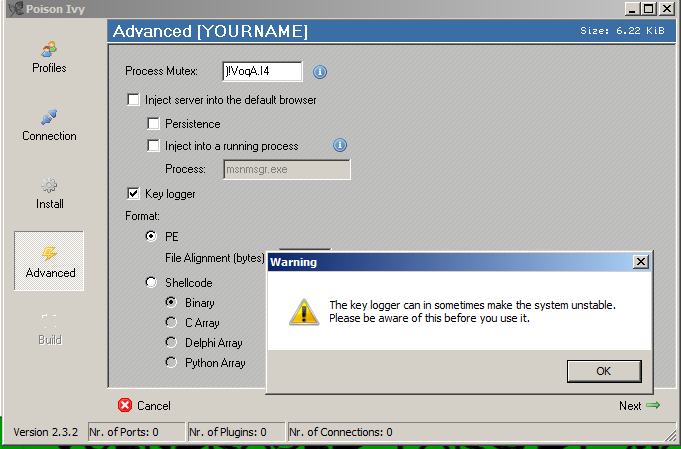
I would like to add over here that this is not my tutorial, i found this tutorial perfect and so i have added this over here. Poison ivy might also be termed a 'remote access trojan'. 1.2 objectives the objective of the mission was.
Because of this the module provides the. Download free tools , hacking tools , poison ivy rat , rat , remote administrator tool. Single thread and single port (inspiration comes from bifrost rat) 增加了wow64的支持,由于uac的问题,有几个功能没有作用,比如activex启动,由于更改了loader,没有时间更改client端的生成功能,最近好忙.
[3] poisonivy stages collected data in a text file. A new fireeye report highlights the resurgence of poison ivy, a malware remote access tool (rat) that. Poisonivy also creates a registry entry modifying the logical disk manager service to point to a malicious dll dropped to disk.
In conjunction with the study, fireeye released calamine, a set of free tools to help organizations detect and examine poison ivy infections on their systems. Screen capturing, video capturing, file transfers, system administration, password theft, and traffic relaying. For example, many cyber criminals use rats to steal personal information, distribute malware, and use them for other malicious purposes.
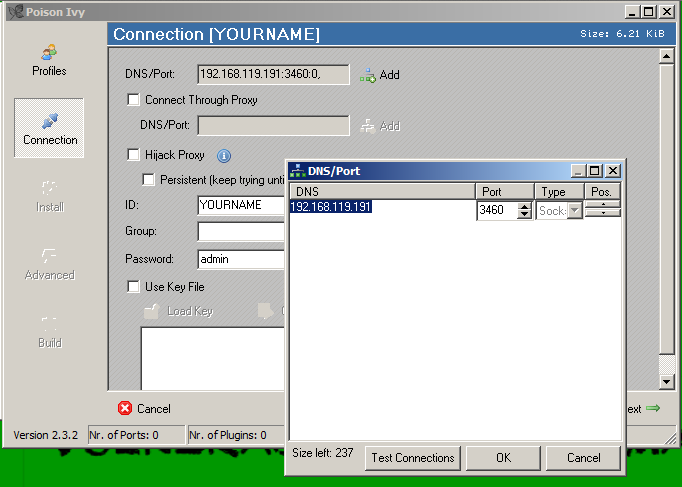
Remote administration tool also known as rat is used to remotely connect and manage single or multiple computers. First released in 2005, the tool has gone unchanged since 2008 with v ersion 2.3.2. Jun 25, 2010 in this tutorial i show you how to use the rat (remote admin tool) poison ivy on a local network.
Information security, scanners and antivirus. Get paid to share your links! External dvd rom for mac.
Security software and hacker tools free download. It provides an attacker with nearly unlimited access to host computer along with screen capture, file management, shell control and device drivers control. Poison ivy hacking tools software, free download windows 7
In case of the c&c configured with another password the exploit can fail. Poison ivy remote administration tool (rat) variants are created and controlled by a poison ivy management program or kit.the poison ivy kit has a graphical user. Here you can download file poison virus maker v2.1.
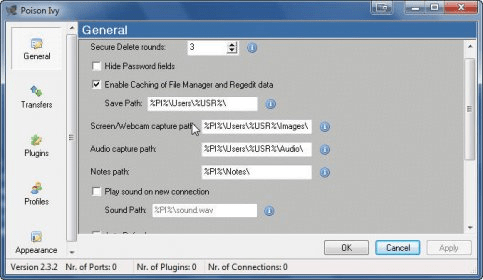
Poison ivy includes features common. Hopefully an exploit try won't crash the poison ivy c&c process, just the thread responsible of handling the connection. Poison ivy crypt m0d by cardx saw v1 mod by legionpr skorpien007 crypter 3.1.
Programs of this type are called remote access or administration tools (rats), however, not all are legitimate and some people use them illegally. Analysis of poison ivy remote access tool. Poison ivy variants are backdoors that are created and controlled by a poison ivy management program or kit.
[3] poisonivy creates a backdoor through which remote attackers can steal system information. [ free download ] poison ivy rat [2.3.2 and full setup ] portable (rat) remote administration tools / remote access trojan by dhs office Other functionality includes viewing a list of open windows or starting.
We based our investigation based on those two facts only. It was used to compromise rsa in 2011. Rat is one of the most dangerous trojan because it compromises features of all types of trojans.
Remote Access Trojan Rat Rat Malware Rat Trojans Malwarebytes Labs Threats
Ratremote Administration Tool
Hack Remote Administration Tools Rat Neon
Project 11 Poison Ivy Rootkit 15 Points
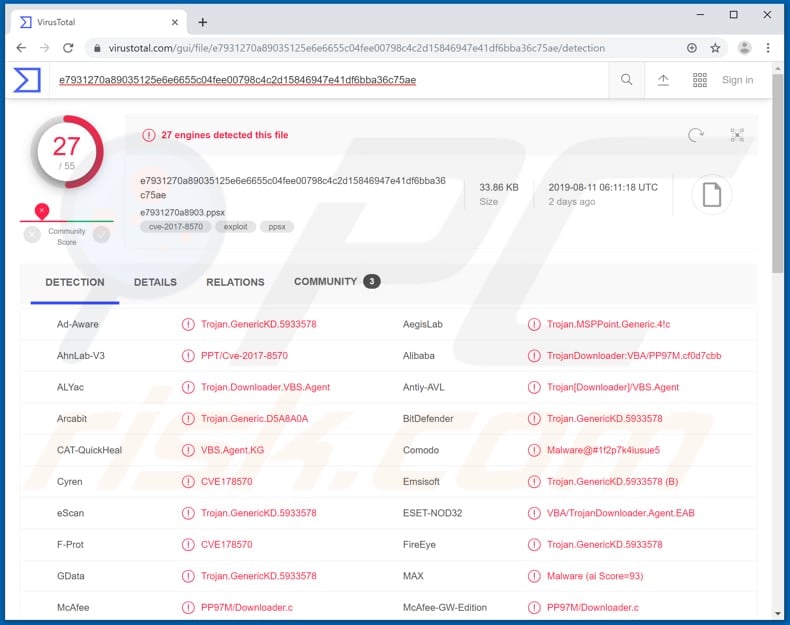
How To Remove Poison Ivy Rat - Virus Removal Instructions Updated
Free Download Poison Ivy Rat 232 And Full Setup Portable Rat Remote Administration Tools Remote Access Trojan By Dhs Office - Dhs Official Web-site
Pi-rat Poison Ivy Remote Access Toolkit Download Scientific Diagram
Remote Administration Tools Rat Hokage04s Blog
Project 11 Poison Ivy Rootkit 15 Points
Poison Ivy 23 Download Free - Poison Ivy 232exe
Project 11 Poison Ivy Rootkit 15 Points
Poison Ivy 23 Download Free - Poison Ivy 232exe
Mandiantcom
Remote Access Trojan Rat Rat Malware Rat Trojans Malwarebytes Labs Threats